According to cloud security software experts the misconfigurations result from a lack of understanding of the cloud platform s shared model.
Aws s3 security vulnerabilities.
To learn about the compliance programs that apply to amazon s3 see aws services in scope by compliance program.
This vulnerability is prevalent in access to s3 buckets in aws.
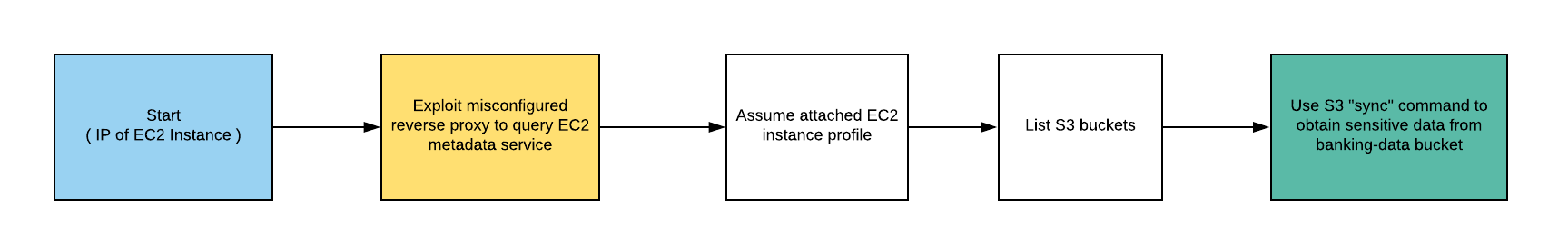
In our last aws penetration testing post we explored what a pentester could do after compromising credentials of a cloud server in this installment we ll look at an amazon web service aws instance from a no credential situation and specifically potential security vulnerabilities in aws s3 simple storage buckets.
Aws s3 common vulnerabilities.
They are all placed in the security misconfiguration category in the detectify tool.
Identify and audit all your amazon s3 buckets enable aws config.
The following security best practices also address configuration and vulnerability analysis in amazon s3.
Rhino security labs is a top penetration testing and security assessment firm with a focus on cloud pentesting aws gcp azure network pentesting web application pentesting and phishing.
This is the most common type of cloud security vulnerability.
If you would like to report a vulnerability or have a security concern regarding aws.
Before we dig deep into the layers of s3 security in our on demand cloud security masterclass register here we thought we d take a quick look at three common ways aws customers put s3 data at risk without realizing it.
Detectify scans for s3 misconfigurations with a severity range between 4 4 9 on the cvss scale.
Another reason is the lack of training.
Continuing from our previous blog basics of aws s3 bucket penetration testing and once you have configured the aws cli setup we will move to exploit the aws s3 bucket vulnerabilities.
Aws s3 buckets are exposing vast quantities of sensitive business data according to a new report from truffle security.
With manual deep dive engagements we identify security vulnerabilities which put clients at risk.
The 6 vulnerability types are.
Aws s3 bucket vulnerabilities could be wormable.
The effectiveness of our security is regularly tested and verified by third party auditors as part of the aws compliance programs.
List permissions on compute resources.
Amazon s3 bucket allows for full anonymous access amazon s3 bucket allows for arbitrary file listing.